Table of Contents
Who is recommending this framework?
➢ Australian Cyber Security Centre is part of the Australian Signal Directorate (ASD)
What is the Framework?
ASD Essential Eight is a prioritized list of mitigation strategies to assist organizations in protecting their infrastructure and data.
Organizations are recommended to implement eight essential mitigation strategies as a baseline. Once organisations have implemented their desired mitigation strategies to an initial level, they should focus on increasing the maturity of their implementation such that they eventually reach full alignment with the intent of each mitigation strategy.
Maturity levels
• There are four Maturity Levels (0-3) that focus on the sophistication of the attacker
• It is up to the organisation to determine the sophistication of a potential adversary
and prepare accordingly
• Things your customers might consider
– their desirability
– their requirement for the confidentiality of their data
– the requirement for the availability and integrity of their systems and data
https://www.cyber.gov.au/acsc/view-all-content/publications/essential-eight-maturity-model
Essential Eight
“Following a review in Cyber resilience the Australian government moves to mandate the essential 8 security
recommendations for all federal departments and agencies as proposed by ACSC (Australian Cyber Security Centre).”
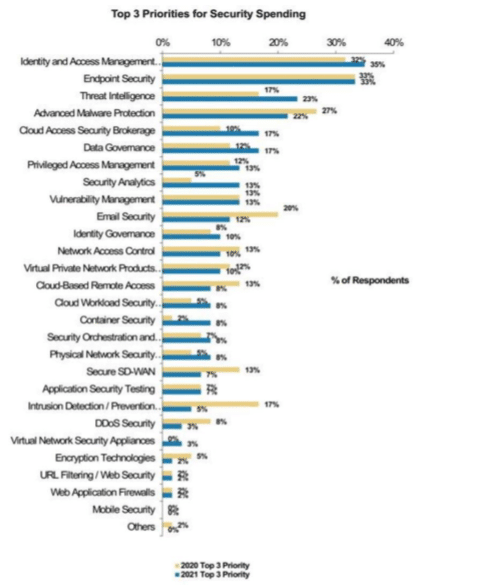
What are the top priorities for
security spending in 2021?
Independent Market Research
Recent Survey of Chief Security Officers conducted by Morgan Stanley Research
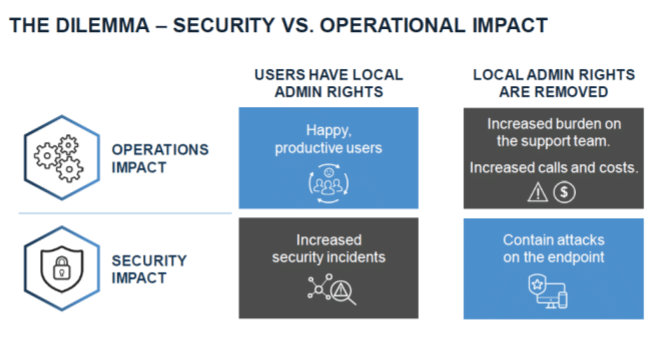
The Problem: Users with admin rights can…
What should an everyday user of a laptop/computer be able to do on it to complete their job function without a huge disruption having to call IT 4 times a week?
where is the balance? see the dilemma below:
➢ Change System Configurations
➢ Install Malware
➢ Access and Change accounts
How you know what the framework is about, how do you get started with implementing this in your business?
Want to know how you can align this to your IT estate and business operations? Contact Us