Table of Contents
Is an email from Google, verified and sitting in your main inbox, always safe? Recent events demand caution. A remarkably sophisticated phishing operation, named “Rockfoils” by Google, exposed how attackers can manipulate trusted digital platforms. This campaign, first brought to widespread public attention in April 2025 through a detailed account by software developer Nick Johnson (@nicksdjohnson on X/Twitter), put potentially billions of Gmail accounts worldwide at risk. It marked a worrying step up from typical phishing methods. The attackers exploited Google’s own infrastructure, achieving a convincing facade of authenticity. This analysis by best IT support in Brisbane examines the campaign’s mechanics, drawing on Johnson’s initial reports and subsequent findings, and outlines essential user protection strategies.
The Attack Mechanism: Crafting False Authenticity
The Rockfoils campaign’s danger originated from its clever exploitation of systems built for user trust. Two core technical strategies were employed:
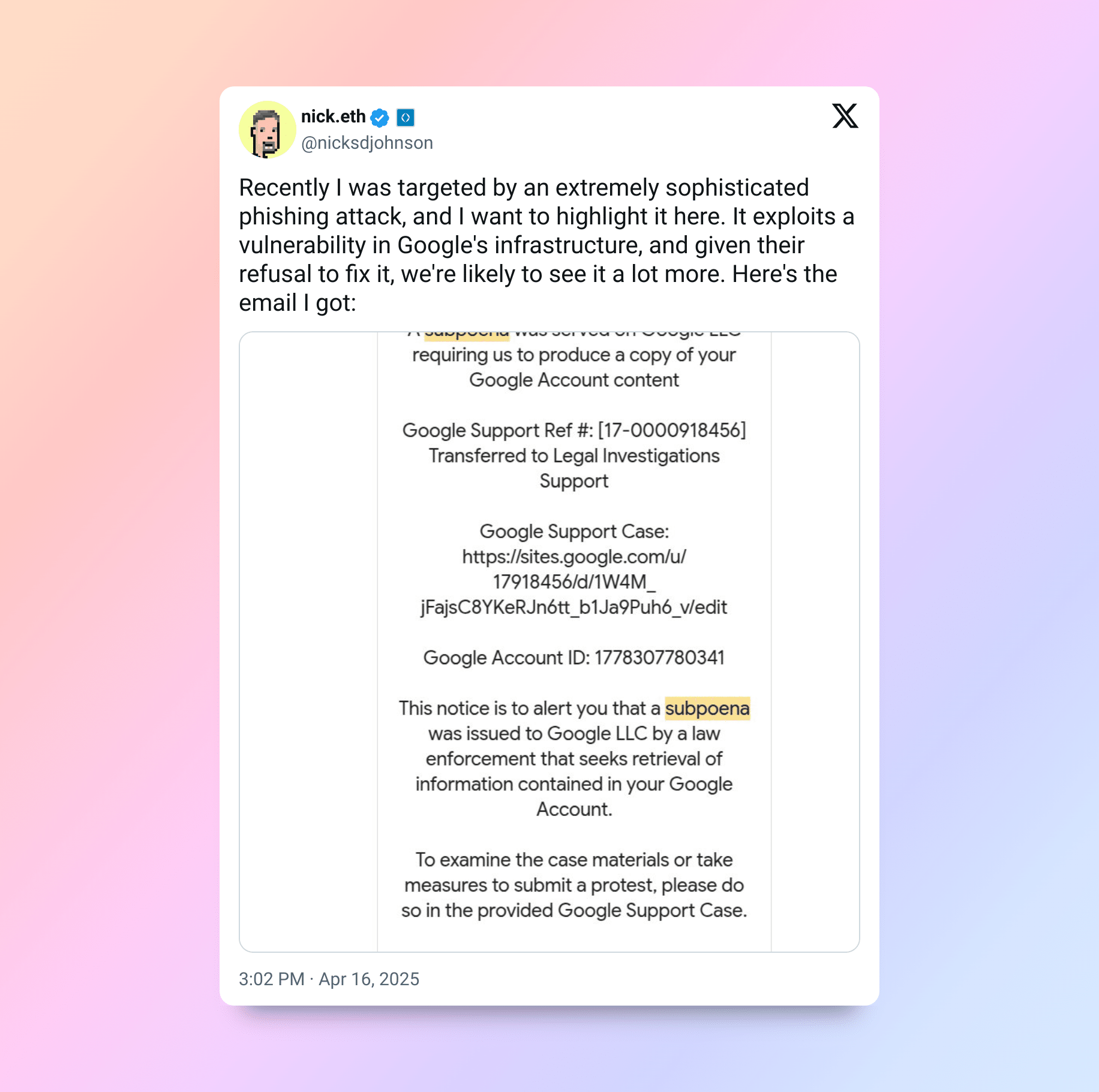
1. DKIM Replay via OAuth Manipulation: This was the attack’s technical linchpin. Adversaries found a vulnerability within Google’s OAuth notification process. They set up a malicious Google OAuth application. Into this application’s name field, they inserted their full phishing message—perhaps a fake legal demand or an urgent security notification. Granting this application access to a controlled Google Workspace account then triggered a standard security alert email from Google. This email, generated by Google’s servers, naturally included the attacker’s message (as the app’s name). Crucially, it was also signed with Google’s valid DKIM (DomainKeys Identified Mail) key. DKIM authenticates email senders. The attackers simply forwarded this officially signed, yet compromised, alert to their targets. The victim’s Gmail saw the valid Google DKIM signature. It allowed the email into the primary inbox. Sometimes, it even appeared within threads containing genuine Google messages, adding to the deception. While Google did sign the message container, the payload was malicious.
2. Leveraging Google Sites for Credential Harvesting: Successfully infiltrating the inbox was just the beginning. The malicious email contained a link. This link didn’t point to an obviously questionable domain but instead to a page hosted on sites.google.com. Google Sites is a legitimate service for creating websites. Here, the attackers built highly convincing replicas of Google’s official sign-in pages or support portals. The familiar google.com address could easily mislead users into believing the site was official, lowering their defences. These counterfeit pages existed purely to harvest credentials: usernames, passwords, possibly even multi-factor authentication codes, all stolen under false pretences.
Analysis of the Attack’s Effectiveness
This campaign proved particularly insidious by undermining standard security guidance. Users are trained to check sender details and look for verification like DKIM. Rockfoils turned these checks against them:
- Authentic Sender: The email displayed [email protected], a known Google address.
- DKIM Passed: It carried Google’s valid DKIM signature.
- Trusted Domain: The phishing page resided under the trusted google.com umbrella.
- Contextual Camouflage: Landing in the primary inbox, sometimes mixed with genuine alerts, created potent camouflage.
This technique wasn’t entirely novel. A similar DKIM replay method targeted PayPal users just weeks before. That attack abused a different platform function but relied on the same core concept: trick the platform into issuing a signed email containing the attacker’s payload, then forward it. The repetition across major platforms points towards a reusable attack pattern, perhaps shared or independently discovered by threat actors. To secure your business from future attacks, search for “small business it services near me” to find the best IT company near by.
Potential Impact: The Scope of Compromise
Gaining unauthorised access to a Google account unlocks far more than just email. Attackers could potentially compromise a user’s entire connected Google ecosystem. This includes:
- Sensitive files within Google Drive.
- Payment details in Google Pay.
- Personal images in Google Photos.
- Contacts, calendars, and location data.
- Third-party service access via “Sign in with Google”.
Such extensive access opens doors to identity theft, direct financial loss, serious data breaches, and using the compromised account for further attacks, like Business Email Compromise (BEC) targeting the victim’s employer or associates. Seek IT help in Brisbane when you suspect an attack.
Mitigation Strategies: Enhancing Account Security
Google confirmed implementing fixes for the specific Rockfoils exploit. The underlying techniques, however, necessitate ongoing user vigilance and strong security habits. Consider these measures essential:
1. Implement Phishing-Resistant Multi-Factor Authentication (MFA): This is the most critical defence. Enable MFA on Google accounts without delay. Choose the strongest available methods:
- FIDO2 Security Keys (e.g., YubiKey, Google Titan Key): Physical devices offering excellent phishing resistance.
- Passkeys: Modern, device-linked keys providing similar robust security.
- Authenticator Applications (e.g., Google Authenticator, Authy): Generate time-sensitive codes; a good fallback.
- Treat SMS codes as a less secure option. Strong MFA blocks logins even if a password is stolen. Google strongly advocates for this.
2. Scrutinise Hyperlinks and Domain Names: Before clicking links, especially those asking for logins, inspect the full URL. Hovering the mouse usually reveals it. Be extremely wary of unexpected subdomains, even under google.com. Genuine Google logins use accounts.google.com or similar official addresses, not sites.google.com.
3. Verify Requests via Direct Navigation: Ignore links or instructions in unsolicited messages about account issues. If concerned, close the message, open a fresh browser tab, and manually type the official service address (e.g., google.com). Log in directly to check for legitimate notifications. Or seek IT services in Brisbane for an additional layer of security.
4. Evaluate Urgency and Threat Claims Critically: Messages demanding immediate action or invoking authority (like subpoenas) aim to bypass rational thought. Pause. Verify independently.
5. Utilise Reporting Mechanisms: Use Gmail’s “Report phishing” feature. This helps refine filters and protects the wider community.
6. Maintain Strict Password Hygiene: Every online account needs a strong, unique password. Use a password manager to handle their creation and secure storage.
Vigilance in an Evolving Threat Landscape
The Rockfoils campaign starkly illustrates attacker adaptability. Its significance lies in weaponising legitimate cyber security Brisbane infrastructure—OAuth notifications, DKIM trust, Google’s own domain name. It showed that traditional email verification isn’t foolproof. A multi-layered defence approach is necessary. Phishing-resistant MFA or Passkeys are fundamental. Platforms must continuously secure their entire infrastructure, not just core services. For users, constant vigilance and adherence to security best practices by managed IT services in Brisbane remain the bedrock of defence against these evolving threats.