Table of Contents
Working from home has its pros and cons. On one hand, it is favorable for businesses because they save on costs by not providing a physical office space. Employees can also work remotely without having to commute daily into town which saves them time and money as well! Of course there are disadvantages compared with traditional workplaces too – you have no coworkers around when you’re working at home, or your boss might be hard to reach if something urgent crops up during off-hours….
When the pandemic hit the world, most workers were forced to work remotely. Most companies weren’t prepared for this major change. IT systems and infrastructure need time to be implemented to allow an efficient and secure home working environment.
In the haste for businesses to remain afloat, Tech Engine Australia are well aware many have neglected cybersecurity. With employees working from home without prior training on security protocols, cyber attacks are an ever-present danger that cannot be ignored.
In this guide, we’ll look at some of the cybersecurity risks of staff working remotely. We’ll also look at the possible solutions to help employees working from home mitigate these risks.

Types of Cybersecurity Risks when Working from Home
1. Phishing
The many emails that you receive when working from home are a cyber attacker’s best chance to trick the unsuspecting employee. Phishing messages often contain links, which could lead workers to malicious sites where personal and company data can get extracted or stolen remotely.
2. Unsecure networks
When a company declares that workers should work from home, most employees will use their home network. If an employee doesn’t have an internet connection at home, they will look towards installing for work purposes.
The IT department at your company is on high alert. For example, they’re always checking for any weak points in their connection to the internet and taking precautions against malware attacks by securing networks with sophisticated protocols.
Your company could be at risk because most employees don’t know how to check for vulnerabilities with their network connections. This means that unsecure networks are likely exposing highly confidential data belonging to your company.
Some employees are even reckless enough to access company and personal data on public networks. These are networks present in cyber cafes, coffee shops, and restaurants.
4. Remote Infrastructure attacks
As companies prepare to send more workers home, they have to expand their infrastructure. Businesses are also expected to monitor the network against attacks and if not careful, this can cost them heavily.
The expansion of infrastructure to accommodate remote workers could increase the risk of DDoS attacks. These are attacks where workers are denied access to the network by scammers.
5. Weak controls
Company data is often protected using layers of security, tight firewalls, and authorization. To access specific data in your home network you need to have an unsecured connection with all the risks that come from it like fraudsters accessing company information or other hackers trying attacking defense systems.
Of course, there are many more potential threats/types of attack such as:
- Malware
- Man-in-the-middle (MitM)
- Denial of service (DoS)
- Phishing
- SQL injection
- Password attack
So it’s as important as ever too address Cyber Security for your company.
Components of Cyber Security
Cybersecurity leverages three main components, namely, technology, processes, and people. We’ll look at each of these components, helping us find solutions to cyber threats.
Technology
To combat cybercrimes, companies need to take advantage of the latest technology to protect their systems. Most fraudsters will target customer data, personnel information, or financial details of the company.
Technology is a useful tool for companies to protect themselves against cyberattacks with deceptive technology. This type of tech can confuse criminals, giving the company more time until an attack makes it past their IT technicians’ defenses and you’re left vulnerable in your tracks.
New technology is making it possible to protect your data on the internet with innovative DNS protection. Tech Engine Australia have teamed up with Webroot, a market leading security company, for an exciting new tool that will help you have peace of mind when browsing the web and suffer less from identity theft as well as malware attacks!
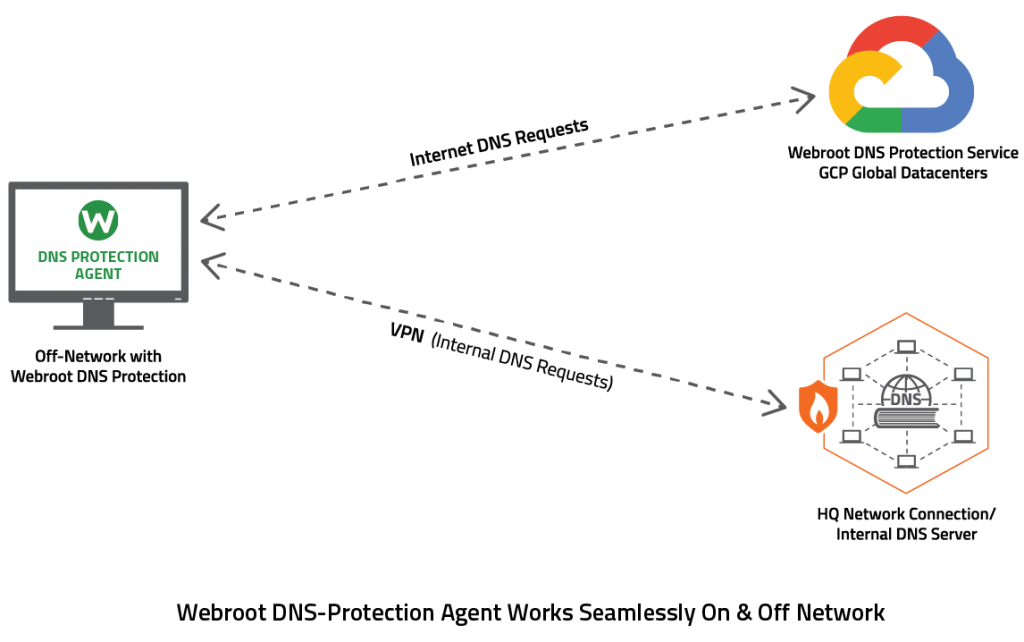
Tech Engine Australia research and test many options on the market. We have carefully chosen Webroot to offer you the best DNS protection which offers multiple advantages:
- This fully cloud-based, secure, and resilient service takes just minutes to set up.
- Get detailed reports on-demand.
- Control internet usage for your users using pre-configured and custom policies by group, device or network.
- Block threats at the domain level
- Webroot® threat intelligence backs all Webroot products, and is trusted by over 100 leading technology vendors to enhance their services.
- DNS filtering stops up to 88% of web-borne malware at the domain layer, so it never reaches your network. It saves you time and money, while also minimizing unproductive web usage.
See more information about Webroot DNS protection here.
Processes
There is no one-size-fits all solution to combat crime. IT professionals take different approaches, but there should be a clear process on how to deal with any form of attack in order for faster response rates and less aggravation when attacks occur.
People
Cybersecurity is an ever-changing, fast paced field. The people are also integral to this effort because they often pose the weakest link in a company’s security chain. Attackers will target employees for these reasons: one being that most of them lack knowledge about how they can put their organization at risk and what level of protection needs to be taken care of on personal devices when using work materials; another reason would be because it is much easier than trying to go through all those firewalls that companies set up against cybercrime as well as anything else protecting data from getting hacked into by outside sources.
As a worker, you must be aware of the dangers that surround your network and protect it from any unforeseen attacks. Training is vital so employees can distinguish between real emails or links to fake ones. Workers should also use different passwords for their personal accounts than what they do at work (employees often reuse passwords). And once an attack has been detected by workers – report immediately!

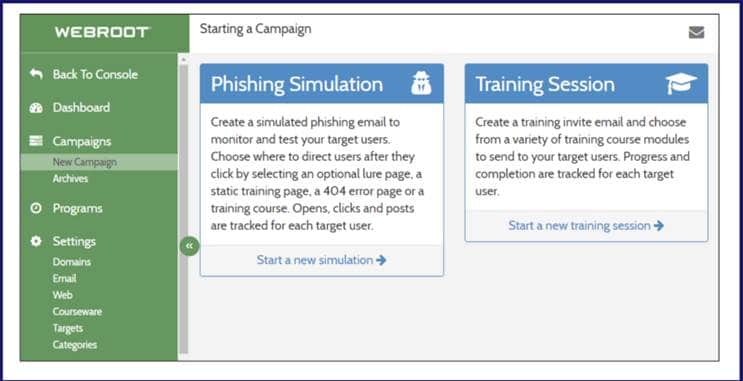
If you’re thinking of training your employees on ways to combat cybercrimes, we’ve got you covered. We’ve partnered with Weebroot to offer a cybersecurity awareness training program. Our program will provide the following benefits to your workforce.
• Send different types of phishing campaigns to your staff and Identify who opens them
• Identify who may need more training
• Provide them with a short training video
• Provide them with a test
Tech Engine Australia feel security awareness training is essential
Although businesses may feel their employees wouldn’t be fooled by something like a phishing scam, Tech Engine Australia have seen many cybercriminals still use this attack method because it continues to be successful. In fact, the 2018 Verizon Data Breach Investigations report revealed that 93% of successful security breaches start with phishing.
To increase security, companies must focus not only on the digital realm but also in their physical location. Train employees to be wary of phishing scams and other methods that could lead to a data breach or infection by providing courses about cybersecurity best practices.
See more information about security awareness training.
Want to learn more about our tool? Contact us today and protect your business.