Table of Contents
This post is to raise awareness for tracking the threats that a relevant to Australian businesses. Most of these cyber threats have a world word reach and cause problems for thousands of businesses.
Australian Cyber Security Centre recent posts
Below are two recent examples of how advanced cyber security threats are affecting Australian businesses. This is why Tech Engine Australia is an expert in cyber security practices to keep your business as safe as it can be.
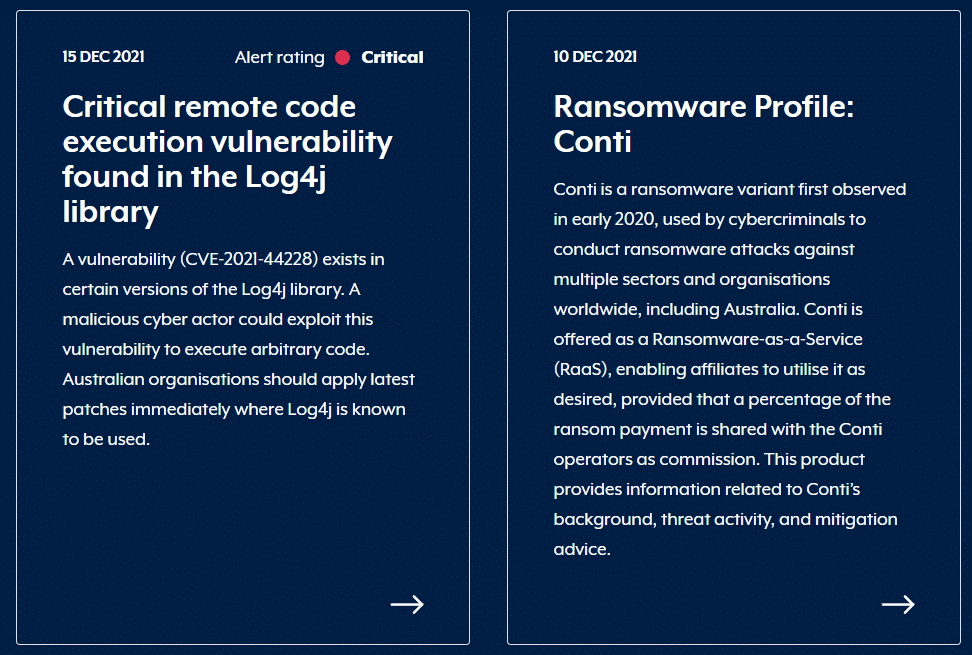
what is Log4j? This is code that is part of Java. Java is used in lots of applications, which opens the scope of the problem up.
What is ransomware? This is malware that encrypts your company data, making it unaccessible, only by paying to get access back. But often after paying, you still can not get access to the data!
Your next steps following reading this post
Take action, review the 3 steps below to be able to complete some basic protection, update your operating system on your devices and computers. Enable multifactor authentication on all of your data-holding applications and tools (if it does not support multi-factor authentication, is it time to upgrade?). Finally, have a copy of the data in another location with multiple copies of the backups.

Next Step
Get a review of your systems and processes to see if there are areas of improvement. The most effective way is to book a session with a consultant.



